| CP4P_Compression-and-Backup.pptx | Lecture PowerPoint slides |
| CP4P_CompressionBackup_Activity_Archive.zip |
Activity Archive (Instructions and Answer docs)
— download and unzip/decompress For any .zip archive, ensure you work with the extracted files.
Yes, you can double click to open a file within a zip archive—the OS automatically extracts it to a deeply buried temporary work folder—but keeping track of those temp files is not as easy as taking a few seconds to do a proper extraction. |
| Show provenance of _Activity_Answers development.docx | How to show you did the work |
Ransomware defence:
Backups:
Have a lot of data to backup? Watch this: https://youtu.be/y2F0wjoKEhg
What “Dead to Me” (Netflix) Taught Us About 3-2-1 BackupHow Nunavut recovered from a ransomware attack
Canadian firm pays $175,000 to recover from ransomware attack.
MapleSEC: The ransomware attack that turned into a horror story
https://www.itworldcanada.com/article/maplesec-the-ransomware-attack-that-turned-into-a-horror-story/436726
Canadian firm pays $425,000 to recover from ransomware attack.
http://www.itworldcanada.com/article/canadian-firm-pays-425000-to-recover-from-ransomware-attack/394844#ixzz4n70bPzrD
"Another lesson apparently is to ensure backups aren’t connected to the primary system."
Because, if your backup is not platform independent, ransomware will encrypt your backups too.
800+ Million Emails Leaked by Email Verification Service
To: verifications.io
Subject: [security alert] Verifications.io emails database exposed to public
Date: February 25, 2019
Ticket ID: #683614
Thank you for reporting the issue. We appreciate you reaching out and informing us. We
were able to quickly secure the database. Goes to show, even with 12 years of experience
you can't let your guard down.
After closer inspection, it appears that the database used for appends was briefly exposed.
This is our company database built with public information, not client data.
As you pointed out, data breaches and ransom are one of the largest threats our industry and
businesses face. We maintain full backups (both offline and in a different geographic
location) so the destruction of data or ransom is not a concern for us. The exposure of PII
(Personally Identifiable Information) to criminals is our primary concern and we take it seriously.
We have taken appropriate measures to correct this.
World Backup Day advice: Give your system some love | IT World Canada News
Pop songs compressed by the Lempel-Ziv algorithm
Huffman coding is a lossless data compression algorithm. It assigns variable-length codes based on the frequency of characters.
Huffman tree building animation:
input text LOSSLESS, move "Animation Speed" slider to left, click [ Build tree
].Huffman Coding
raw text: LOSSLESS <== 8 char X 8 bits = 64 bits
charArray: L O S E <== unique chars in text
countArray: 2
1 4
1 <== count char in text
Huff.Code: 10 110 0 111 <== variable-length binary based on frequency of characters (see tree below)
encode: 10 110 0 0 10 111 0 0 <== substitute each char in text for Huffman code, 14 bits or 22% of original
Frequency Table (Char, Frequency, bit length) : (S,4,1)(L,2,2)(E,1,3)(O,1,3) data to build binary tree for decoding.
charArray and countArray used to create binary tree resulting in shortest path to the most frequent characters.
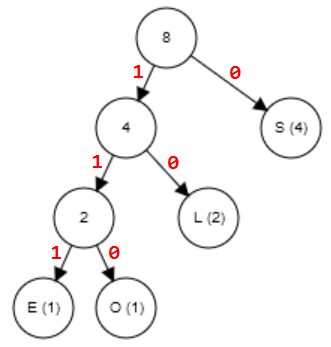
Decode logic:
For each encoded bit
{ traverse binary tree trunk (0 right, 1 left) IF at leaf node
{ get/print char; reposition at binary tree root node;
}
}